You can also read my newsletters from the Substack mobile app and get notified when a new newsletter issue comes out.
Did you know many companies find critical vulnerabilities in their systems only after a security breach?
You don’t want to be one of them, managing fallout instead of prevention.
Amazon Inspector can help.
It continuously checks your AWS environment for security issues, ensuring you're always one step ahead.
In this newsletter issue, I will cover:
What is Amazon Inspector?
Key Features
Setting up Amazon Inspector
Running Assessments
Understanding Amazon Inspector Findings
Integration with DevOps Practices
Compliance
Limitations and Considerations
Best Practices
Source: Unsplash
What is Amazon Inspector?
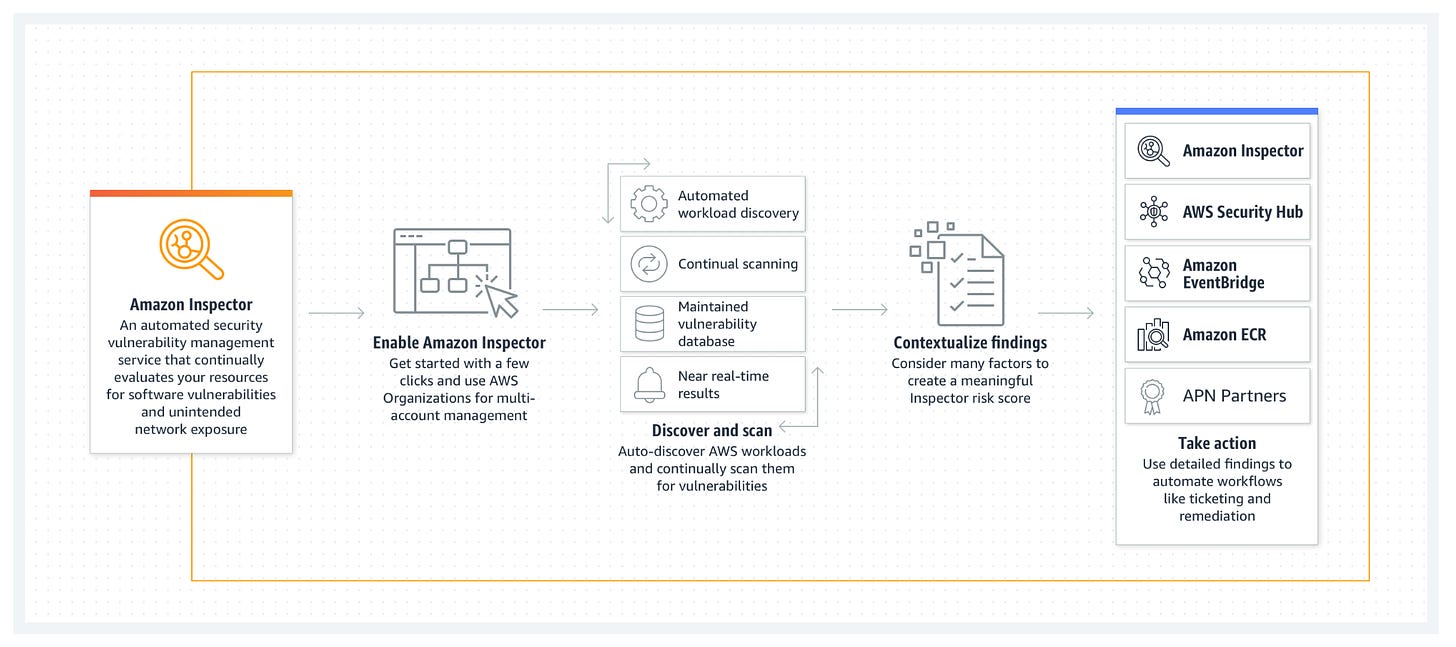
Amazon Inspector is an automated service that provides security assessments within Amazon Web Services (AWS).
It checks for security vulnerabilities and deviations from best practices across your AWS infrastructure, focusing primarily on your applications and their underlying resources.
Amazon Inspector analyzes the behavior of running instances and offers detailed security reports to guide remediation efforts.
Source: Amazon Inspector
How Amazon Inspector Works
Amazon Inspector operates by automatically scanning your AWS resources. Here’s a basic rundown of its operation:
Setup: You define the assessment targets—the AWS resources you want to evaluate, such as EC2 instances and their associated applications.
Assessment Templates: You select templates that specify the types of security checks to run. These templates are based on industry best practices and common compliance requirements.
Running the Assessment: Once initiated, Amazon Inspector performs security assessments using the defined templates. It examines the running environments and configurations for potential security issues.
Reporting: After the assessment completes, Amazon Inspector provides detailed findings that include descriptions of potential vulnerabilities, their severity, and recommendations for mitigation.
Types of Assessments
Amazon Inspector can conduct two main types of assessments:
Network Assessments: These focus on network configurations and security, checking for unauthorized access or vulnerabilities in how network traffic is managed.
Host Assessments: These evaluate the operating system and installed applications for vulnerabilities, including common issues like outdated software or insecure system configurations.
Key Features
Amazon Inspector is designed to enhance the security of your AWS environment through a set of powerful features. Understanding these features can help you better utilize this tool to safeguard your applications and data.
Automated Security Assessments
Amazon Inspector automates the process of security vulnerability assessments on your AWS resources. Once set up, it continuously evaluates your environment against a pre-defined set of security rules, reducing the need for manual security audits. This automation helps in identifying vulnerabilities early and ensures consistent security checks without human intervention.
Integration with AWS
Amazon Inspector is deeply integrated with other AWS services, enhancing its functionality and ease of use:
AWS Identity and Access Management (IAM): Inspector uses IAM to securely perform assessments without requiring manual credentials management.
Amazon CloudWatch: You can set up alarms and notifications based on Inspector findings directly through CloudWatch, allowing for real-time security incident response.
AWS Lambda: Automate responses to security findings using Lambda functions. For example, you can automatically patch vulnerabilities when they are detected.
This integration streamlines security processes and leverages the AWS ecosystem to provide a more robust security posture.
Scalability
One of the key advantages of Amazon Inspector is its scalability.
Amazon Inspector can scale to meet your needs, whether you're managing a few instances or thousands.
This is particularly beneficial in dynamic environments where AWS resources can fluctuate.
Inspector's scalability ensures that your expanding infrastructure remains under continuous assessment without requiring manual configuration changes.
Setting up Amazon Inspector
Setting up Amazon Inspector is a straightforward process that involves a few key steps.
Here’s a guide to help you get started with using Amazon Inspector to assess the security of your AWS resources.
Required Permissions and Roles
To use Amazon Inspector, you need specific permissions and roles configured in AWS Identity and Access Management (IAM):
IAM Role for Amazon Inspector: Create an IAM role that allows Amazon Inspector to access the necessary resources within your AWS account. This role needs permissions to interact with services such as Amazon EC2 and AWS Systems Manager.
Attach Policy: Attach the AmazonInspectorServiceRolePolicy to the IAM role. This policy grants Amazon Inspector the permissions it needs to perform security assessments.
Choosing and Configuring Assessment Templates and Rules
Amazon Inspector uses assessment templates to determine what rules to apply when scanning your resources:
Select a Template: Choose a predefined assessment template based on the type of assessment you want to conduct (e.g., network or host assessment). Templates are configured to check for vulnerabilities and deviations from best practices.
Configure Assessment Rules: Each template includes a set of rules. You can customize which rules to enable based on your specific security needs. These rules determine the checks that Amazon Inspector will perform, such as looking for exposed confidential data or checking for vulnerabilities in installed software.
Setting Up Assessment Targets
Define what AWS resources Amazon Inspector should assess:
Select Resources: Define the resources you want to assess, such as specific EC2 instances or entire VPCs. This is done by tagging the resources or by specifying the resource IDs.
Assign Resources to Templates: Link your chosen resources to the assessment templates to ensure that the right types of assessments are performed on the appropriate resources.
Running Assessments
Once Amazon Inspector is set up and configured, running security assessments on your AWS resources is a systematic process. Here’s how to initiate and manage these assessments effectively.
Initiating a Security Assessment
To start an assessment using Amazon Inspector:
Launch an Assessment: Navigate to the Amazon Inspector console in your AWS account. Select the assessment template you've configured and click 'Start' to begin the assessment. You can start assessments manually or schedule them to run at regular intervals, depending on your needs.
Assessment Duration: Specify how long the assessment should run. A typical assessment might run for several hours to ensure a thorough evaluation, but the duration can be adjusted based on the complexity and size of the environment.
Understanding Assessment Targets and Templates
Assessment Targets: These are the specific AWS resources you have chosen to assess, such as EC2 instances. Ensure that the targets are correctly tagged and linked to the appropriate assessment template to guarantee accurate results.
Assessment Templates: These define the rules and conditions under which your resources are evaluated. Each template is tailored to either network or host assessments and includes a set of rules that Amazon Inspector applies during the assessment.
Interpreting the Assessment Report
At the end of an assessment, Amazon Inspector generates a detailed report that includes:
Findings: Each finding is a potential security issue discovered during the assessment. Findings are categorized by severity (low, medium, high, critical) to help prioritize remediation efforts.
Recommendations: For each finding, Amazon Inspector provides recommendations on how to address the issue. This might include patching software, changing configurations, or enhancing security policies.
Resource Details: The report also details which resources were affected and provides information about the specific vulnerabilities or compliance deviations found.
The report generated by Amazon Inspector is a valuable resource for understanding the security vulnerabilities within your AWS environment. By regularly running assessments and addressing the findings, you can significantly enhance the security and compliance of your cloud infrastructure.
Understanding Amazon Inspector Findings
Amazon Inspector provides detailed findings that are crucial for maintaining the security of your AWS infrastructure.
Here’s how to understand and manage these findings effectively.
Types of Vulnerabilities Detected
Amazon Inspector can identify a range of security vulnerabilities and deviations from best practices, including:
Common Vulnerabilities and Exposures (CVEs): These are publicly known security vulnerabilities in software that Amazon Inspector can detect based on the versions of installed software.
Insecure Configurations: This includes improperly configured access settings or permissions that could allow unauthorized access.
Unintended Network Accessibility: Amazon Inspector checks if sensitive ports are unnecessarily exposed to the internet, potentially allowing attackers to exploit them.
Severity Levels
Amazon Inspector classifies its findings into four severity levels:
Low: Issues that represent minimal risk and often require minimal action unless they are part of a broader security weakness.
Medium: Issues that should be addressed but do not pose immediate critical threats.
High: Serious vulnerabilities that could be exploited in the short term and should be prioritized for remediation.
Critical: Top-priority issues that pose an immediate risk to the system's security or data integrity and require urgent attention.
Understanding the severity levels helps prioritize which issues to address first, allowing you to allocate resources more effectively to mitigate risks.
Best Practices for Responding to and Mitigating Issues
To efficiently address the findings from an Amazon Inspector assessment, consider the following best practices:
Immediate Action on High and Critical Findings: Prioritize fixing high and critical issues as quickly as possible to reduce the risk of exploitation.
Systematic Review of Medium and Low Findings: Schedule regular reviews for medium and low severity findings. While these are less urgent, they can still pose risks if not addressed over time.
Patch Management: Regularly update and patch software to protect against known vulnerabilities that Amazon Inspector identifies.
Configuration Management: Review and improve configuration settings based on the recommendations from Amazon Inspector to enhance security.
Automate Responses: Use AWS services like AWS Lambda to automate responses to common issues identified by Amazon Inspector, such as patching vulnerabilities or modifying configurations.
By systematically addressing the findings from Amazon Inspector and integrating these best practices into your ongoing security strategy, you can significantly improve the security and resilience of your AWS environment.
Integration with DevOps Practices
Integrating Amazon Inspector into your DevOps practices can significantly enhance the security posture of your development lifecycle.
Here’s how to seamlessly incorporate this tool into your continuous integration and continuous deployment (CI/CD) processes.
Fitting Amazon Inspector into CI/CD Pipelines
Automated Security Checks: Incorporate Amazon Inspector as a step in your CI/CD pipeline to automatically assess new or updated code for vulnerabilities before deployment. This ensures that any new release is scanned for security issues, preventing potential vulnerabilities from reaching production environments.
Continuous Assessment: Configure Amazon Inspector to continuously assess your running environments in AWS, providing ongoing security assurance and compliance checks throughout the software lifecycle.
Feedback Loops: Use the findings from Amazon Inspector to inform development teams about security issues. Integrating these insights back into the development process helps in correcting security vulnerabilities early and improving the security awareness of your development teams.
Automating Security within the DevOps Lifecycle
Integration with Build Tools: Connect Amazon Inspector with your build tools like Jenkins, CircleCI, or Travis CI. This allows automated triggering of security assessments each time the build process runs, embedding security checks directly into the development process.
Notification Systems: Set up notifications to alert teams about critical findings directly through communication tools such as Slack, email, or AWS Simple Notification Service. This immediate feedback can accelerate the remediation process by ensuring that the right people are informed in real-time.
Compliance
Amazon Inspector plays a pivotal role in helping organizations maintain compliance with various external regulations and standards.
Here’s how it can support your compliance efforts effectively.
Role of Amazon Inspector in Compliance
Automated Compliance Checks: Amazon Inspector can automatically check for compliance with security best practices and regulatory standards. It assesses your AWS resources against a library of compliance rules and generates detailed reports on your compliance status.
Continual Compliance Monitoring: By continuously monitoring your environment, Amazon Inspector helps ensure that your infrastructure remains in compliance over time, even as changes are made. This is crucial for maintaining compliance in dynamic cloud environments where configurations can frequently change.
Specific Compliance Frameworks Supported
Amazon Inspector can assist with compliance across several key frameworks:
PCI-DSS: For organizations that handle credit card information, Amazon Inspector can check for vulnerabilities that might jeopardize your PCI-DSS compliance, such as unsecured data transmissions or improper authentication controls.
HIPAA: For healthcare organizations, Amazon Inspector can help ensure that the infrastructure complies with HIPAA standards by identifying security issues that could affect the protection of PHI (Protected Health Information).
GDPR: While GDPR compliance involves broad data protection measures, Amazon Inspector can contribute by identifying security risks that could lead to data breaches, thereby impacting GDPR compliance.
Leveraging Amazon Inspector for Compliance Efforts
Tailored Assessments: Customize assessment templates in Amazon Inspector to focus on specific compliance needs. For example, create templates that specifically target controls and checks relevant to the regulatory frameworks you need to comply with.
Documentation and Reporting: Use the detailed findings and reports generated by Amazon Inspector as part of your compliance documentation. These reports can provide audit trails for compliance audits and demonstrate ongoing due diligence in security practices.
Limitations and Considerations
While Amazon Inspector is a powerful tool for security assessment, there are some limitations and considerations to be aware of when integrating it into your AWS environment.
Potential Limitations
Coverage: Amazon Inspector focuses on specific AWS resources and the AWS environment. It may not cover all aspects of security, such as application-level vulnerabilities that require more specialized tools.
Scope of Detection: The effectiveness of Amazon Inspector depends on the predefined rules and templates it uses. It might not detect new or emerging threats that have not yet been included in its rule sets.
Region Availability: Amazon Inspector is not available in all AWS regions. This limitation can affect organizations operating globally who need consistent security practices across multiple geographic locations.
Costs Associated with Amazon Inspector
Pricing Model: Amazon Inspector is charged based on the number of assessments run and the size of the assessed resources. It’s important for organizations to consider these costs, especially when scaling up their use of AWS services.
Assessment Frequency: Running frequent assessments can lead to higher costs. Organizations need to balance the need for regular security checks with the associated expenses.
Scenarios Where Amazon Inspector Might Not Be the Best Fit
Non-AWS Environments: For organizations using multi-cloud or hybrid environments, Amazon Inspector cannot assess non-AWS resources, which might necessitate additional security tools.
Advanced Threat Detection: Organizations facing advanced security threats may require more sophisticated security solutions that offer proactive threat hunting and advanced anomaly detection beyond the capabilities of Amazon Inspector.
Best Practices
Utilizing Amazon Inspector effectively requires understanding its capabilities and integrating it seamlessly into your security protocols.
Here are some best practices to ensure you get the most out of Amazon Inspector:
Regularly Update Assessment Rules
Stay Updated: Amazon Inspector's rules are regularly updated to include the latest vulnerability definitions and compliance requirements. Regularly updating the rules used in your assessments ensures that your checks are current and effective.
Customize Rules: Tailor the rules to fit the specific needs of your organization. This customization can help focus your assessments on the most relevant threats and compliance requirements.
Schedule Frequent Assessments
Continuous Monitoring: Set up a schedule for regular assessments to ensure continuous monitoring of your environment. Frequent assessments help catch vulnerabilities as they arise, particularly important in dynamic cloud environments where changes are constant.
Automate Assessments: Automate the triggering of assessments to coincide with deployment cycles or when changes are made to your AWS resources. This automation helps integrate security assessments into your DevOps practices seamlessly.
Prioritize and Address Findings
Severity Levels: Focus on addressing findings categorized as high or critical severity first, as these represent the most significant risks to your environment.
Remediation Plans: Develop clear remediation plans for addressing identified vulnerabilities. Include timelines and responsibilities to ensure that issues are resolved promptly.
Leverage Integrations with Other AWS Services
Security Information and Event Management (SIEM): Integrate Amazon Inspector with AWS security services like Amazon CloudWatch and AWS Security Hub. This integration allows for comprehensive monitoring and easier management of security alerts.
Automated Responses: Use AWS Lambda to automate responses to common security findings, such as patching known vulnerabilities or adjusting security groups in response to detected threats.
Continuously Improve Security Postures
Feedback Loops: Use the insights gained from Amazon Inspector assessments to improve your security measures and policies continually. Adjust configurations, update policies, and enhance security practices based on assessment outcomes.
Staff Training: Educate your team about the importance of security and the specific role of Amazon Inspector in your security strategy. Ensuring that your staff understands how to use Amazon Inspector effectively can enhance your overall security posture.
Conclusion
As you will have learned by now, Amazon Inspector is a vital tool for enhancing security and compliance within your AWS environment.
From setting up and running assessments to understanding and addressing findings, Amazon Inspector offers a robust framework to safeguard your infrastructure against vulnerabilities.
Following are some key takeaways:
Automated Security Assessments: Amazon Inspector automates the process of security vulnerability assessments, making it easier to identify and mitigate risks continuously.
Integration and Scalability: With seamless integration into the AWS ecosystem and scalable capabilities, Amazon Inspector adapts effortlessly as your AWS usage grows.
Compliance Support: By aiding in compliance with standards such as PCI-DSS and HIPAA, Amazon Inspector is not just a security tool but also a compliance ally.
Continuous Improvement: The tool not only identifies security risks but also provides actionable insights and recommendations, fostering an environment of continuous security improvement.
Cost and Limitations: Be mindful of the costs associated with frequent assessments and understand the limitations of Amazon Inspector, especially in non-AWS environments.
Amazon Inspector is an indispensable part of any AWS security strategy. Whether you’re a software developer, a DevOps engineer, or a cloud architect, integrating Amazon Inspector into your security practices will provide you with a stronger defense against potential threats.
If you have any observations or views about this post, please leave a comment.
Shoutout
My 25-Year Engineering Career Retrospective by
: Lot of valuable lessons to learn from Nicola’s engineering career. Don’t miss out.How to recognize the potential in engineers by
: Checkout Gregor’s top 3 traits to recognize potential in engineers.Multi Version Concurrency Control by
: Deep dive on what is multi version concurrency control.
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Whenever you’re ready, there are 2 ways I can help you:
Are you thinking about getting certified as a Google Cloud Digital Leader? Here’s a link to my Udemy course, which has helped 5+ students prepare and pass the exam. Currently, rated 4.69/5. (link)
Course Recommendation: AWS Courses by Adrian Cantrill (Certified + Job Ready):
ALL THE THINGS Bundle (I got this. Highly recommend it!)
Note: These are affiliate links.
Get in touch
You can find me on LinkedIn or X.
If you wish to request a topic you would like to read, you can contact me directly via LinkedIn or X.






Thanks for the mention Amrut!