TCP # 12 - When it comes to AWS security, knowing 'what' isn't enough
Learn 'how' with this deep dive into SIEM.
You can also read my newsletters from the Substack mobile app and get notified when a new newsletter issue comes out
Did you know that over 70% of companies feel overwhelmed by the volume of security alerts they receive?
That's probably you, too, trying to make sense of what each alert means.
With Security Information and Event Management (SIEM) solution on your side, you decode these alerts and learn the exact steps to tackle them efficiently.
Don't just know there's a problem—know how to fix it with SIEM.
In this newsletter issue, I will cover:
Introduction to SIEM
SIEM Tools within AWS
Architecture of an SIEM solution in AWS
Implementation Steps for Setting Up SIEM in AWS
Best Practices for Optimizing SIEM in AWS

Introduction to SIEM
SIEM is a security system that combines two key functions:
Security Information Management (SIM) and Security Event Management (SEM).
It helps organizations manage their security by gathering and analyzing data from various sources in real-time. This helps detect issues and prevent potential security breaches.
Why SIEM?
SIEM systems are essential in modern IT environments where data from applications, networks, and cloud services need constant monitoring. They help detect unusual activities that might indicate a security threat.
Importance of SIEM in Cloud Security
Centralized Security Management: Using SIEM in cloud environments like AWS allows businesses to centralize their security management. As companies use more cloud services, managing security across all these services becomes challenging. SIEM simplifies this by collecting and analyzing data from all cloud resources in one place.
Benefits of SIEM
1. Threat Detection
Quick Identification: SIEM systems quickly identify potential security threats by analyzing the patterns in the data collected.
Proactive Security: This early detection helps businesses act swiftly to prevent potential breaches before they cause harm.
2. Improved Incident Response
Automated Alerts: SIEM systems automatically alert security teams about potential threats, which helps in faster response.
Streamlined Processes: By having all security information in one place, SIEM systems streamline the process of managing security incidents.
3. Compliance Management
Regulatory Compliance: SIEM helps businesses comply with laws and regulations by ensuring all necessary security logs are collected, stored, and accessible.
Audit Preparation: It also simplifies the audit process by providing comprehensive reports on security data and incident handling.
4. Visibility and Reporting
Real-Time Oversight: SIEM provides a dashboard view of security events, giving teams real-time insights into their IT environment.
Detailed Reports: It generates detailed reports that help in understanding the security events and system status, aiding in strategic planning and operational adjustments.
SIEM Tools within AWS
AWS offers a suite of tools that serve as the building blocks for implementing a SIEM solution. These tools are designed to work together seamlessly, providing comprehensive security monitoring, threat detection, and compliance management.
Key AWS Tools for SIEM
1. Amazon GuardDuty
GuardDuty is a threat detection service that continuously monitors for malicious or unauthorized behavior to help protect your AWS accounts and workloads.
It uses machine learning, anomaly detection, and integrated threat intelligence to identify and prioritize potential threats.
GuardDuty offers automatic detection of common threats such as unusual API calls or potentially unauthorized deployments that can indicate a possible security breach.
2. AWS Security Hub
Security Hub gives you a comprehensive view of your high-priority security alerts and compliance status across your AWS accounts.
It aggregates, organizes, and prioritizes security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie, as well as from AWS Partner solutions.
The tool provides a unified security and compliance dashboard that helps streamline security management.
3. Amazon CloudWatch
While primarily a monitoring service for AWS cloud resources and applications, CloudWatch can be effectively used for SIEM to observe and respond to system-wide security incidents.
It collects monitoring and operational data in the form of logs, metrics, and events, providing a unified view of AWS resources, applications, and services that run on AWS and on-premises servers.
CloudWatch supports incident response and operational health monitoring by allowing automated responses to certain thresholds and conditions.
4. AWS CloudTrail
CloudTrail is essential for SIEM as it enables governance, compliance, operational auditing, and risk auditing of your AWS account.
It provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
This service is crucial for detecting unusual activity in your AWS accounts and for conducting forensic investigations on potential security incidents.
Integration with Third-Party SIEM Tools
AWS and External SIEM Solutions: AWS provides extensive APIs that allow integration with many third-party SIEM solutions, enhancing the ability to use existing security infrastructure.
This integration helps in creating a robust SIEM architecture that leverages both AWS-native and external resources for a comprehensive security strategy.
Architecture of an SIEM solution in AWS
Understanding the architecture of a SIEM solution in AWS is crucial for effective implementation and operation.
A well-planned architecture ensures that all components are correctly aligned to capture, analyze, and respond to security data efficiently, which is essential for maintaining a strong security posture in cloud environments.
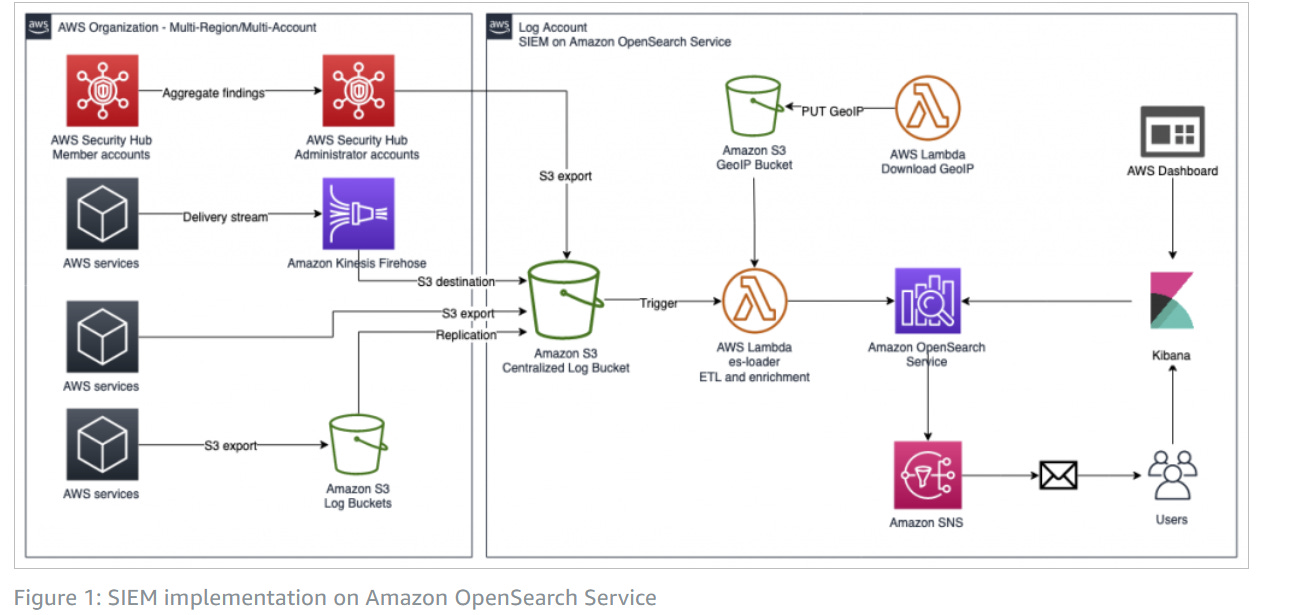
Key Components of SIEM Architecture in AWS
1. Data Sources
Types of Data
AWS CloudTrail Logs: Essential for auditing API and console actions across AWS services.
VPC Flow Logs: Capture information about the IP traffic going to and from network interfaces in VPCs.
DNS Logs: Track DNS queries to help detect malicious domain interactions.
Application Logs: Application-specific logs provide insights into the behaviors and outputs of custom applications.
Collection Methods
Amazon Kinesis: Utilized for real-time data streaming, enabling immediate analysis and processing of security data streams.
AWS S3: Acts as a central repository for storing log data, where logs are archived for long-term analysis and backup.
2. Data Aggregation and Storage
Central Repository
Amazon S3 Buckets: Used for the consolidated storage of logs and historical data, facilitating easier access and management.
Data Aggregation
AWS Glue: A fully managed extract, transform, and load (ETL) service that prepares and loads data for analytics, enhancing the efficiency of data analysis workflows.
3. Data Processing
Real-Time Analysis
Amazon Kinesis or AWS Lambda: These services are leveraged for the real-time processing of data streams and event correlation, enabling immediate detection of potential security events.
Batch Processing
AWS Batch: Efficient for processing large volumes of log data that do not require real-time analysis, optimizing resource allocation and processing time.
4. Threat Detection and Analysis
Threat Detection Tools
Amazon GuardDuty: Offers automated threat detection services that continuously monitor for suspicious activity and unauthorized behavior across your AWS infrastructure.
Custom Analysis
AWS Lambda: Enables the creation of custom rules and analytics tailored to specific organizational security needs, providing flexibility in threat detection.
5. Dashboard and Visualization
Visualization Tools
Amazon QuickSight or AWS Security Hub: These tools provide powerful visualization capabilities for analyzing security data, offering built-in dashboards and the ability to create custom visualizations.
Custom Dashboards
Amazon OpenSearch Dashboards: Facilitates the creation of custom dashboards that cater to specific organizational requirements, enhancing the monitoring and analysis of security events.
6. Alerting and Incident Response
Alert Mechanisms
Amazon SNS: Configured to send immediate notifications upon detection of significant events, ensuring rapid response to potential threats.
Automated Response
AWS Lambda: Executes automated response actions based on specific triggers detected by the SIEM system, enhancing the speed and efficiency of the response.
7. Compliance and Reporting
Compliance Management
AWS Config and AWS Security Hub: These tools are crucial for ensuring adherence to regulatory frameworks, providing continuous monitoring and compliance assessments.
Reporting
Automated Reports: Generate reports automatically for audits and compliance checks, leveraging both AWS services and custom Lambda functions to streamline the process.
Design Considerations for SIEM in AWS
Scalability
Utilize services like Amazon Kinesis for data streams to ensure that the architecture can scale as data volumes grow.
Security
Implement best practices for securing the SIEM infrastructure, including proper IAM roles and policies.
Cost Management
Optimize costs by managing storage effectively and using tools like AWS Cost Explorer to monitor and manage SIEM expenses efficiently.
Implementation Steps for Setting Up SIEM in AWS
The following comprehensive guide provides a structured approach to setting up a SIEM system in AWS, covering everything from initial planning and tool selection to configuration, monitoring, alerting, incident response, and compliance.
Each step is designed to ensure a robust and effective security monitoring framework tailored to the specific needs of an AWS environment.
Preliminary Planning
Define Security Objectives
Identify Key Assets: Begin by cataloging critical assets that require monitoring. This includes applications, data storage, and network infrastructure components vital to your business operations.
Risk Assessment: Conduct a comprehensive risk assessment to identify potential threats and vulnerabilities that could impact these key assets. This step is crucial for tailoring the SIEM setup to your specific security needs.
Choose the Right Tools
Select AWS SIEM Tools: Evaluate and select AWS tools that align with your security objectives. Common choices include AWS Security Hub, GuardDuty, and CloudTrail, each offering unique capabilities for threat detection and compliance monitoring.
Third-Party Tools: Consider the need for third-party SIEM solutions that can complement AWS tools, especially if specific features or integrations are required that AWS does not provide.
Configuration and Setup
Set Up Data Collection
Enable AWS CloudTrail: Ensure that CloudTrail is enabled across all relevant AWS accounts to capture detailed API activity and interactions with AWS resources, providing a foundational dataset for security analysis.
Configure Log Sources: Set up and configure logging for critical AWS services, including VPC Flow Logs, ELB Logs, and access logs for services like S3, to ensure comprehensive visibility into network and resource access patterns.
Establish Data Aggregation and Storage
Centralize Log Storage: Utilize Amazon S3 to create a centralized repository for storing all log data, facilitating secure, scalable, and accessible log management.
Data Aggregation: Configure AWS Glue to aggregate logs from various sources. This step is essential for preparing data for effective analysis, ensuring that data from different environments can be correlated and analyzed cohesively.
Implement Data Processing and Correlation
Deploy Amazon Kinesis: Use Amazon Kinesis for real-time data streaming capabilities, enabling timely processing of security data that is critical for rapid threat detection and response.
Use AWS Lambda: Develop and deploy AWS Lambda functions for custom data correlation and analysis, allowing for tailored detection mechanisms that are specifically designed to meet organizational security requirements.
Activation and Monitoring
Configure Threat Detection
Set Up GuardDuty: Activate and configure Amazon GuardDuty to leverage its automated threat detection capabilities, which analyze vast quantities of data to identify unexpected and potentially unauthorized or malicious activity.
Custom Detection Rules: Create and implement custom detection rules using AWS Lambda to address specific security concerns unique to your organization, enhancing the sensitivity and relevance of threat detection mechanisms.
Establish Monitoring Dashboards
Use Amazon QuickSight or OpenSearch Dashboards: Deploy visualization tools such as Amazon QuickSight or OpenSearch Dashboards to create intuitive, interactive dashboards for real-time monitoring of security alerts and metrics.
Custom Dashboards: Build custom dashboards tailored to the specific monitoring needs and priorities of your organization, enabling more detailed and focused security insights.
Alerting and Response
Set Up Alerting Mechanisms
Configure SNS: Implement Amazon Simple Notification Service (SNS) for robust, real-time alerting that can notify security personnel of critical issues via SMS, email, or other communication channels.
Email and SMS Alerts: Ensure that alerts are set up to reach the right people quickly and efficiently, facilitating swift action when security incidents occur.
Automate Incident Response
AWS Lambda for Automation: Utilize AWS Lambda to automate response actions to common types of security alerts, such as isolating compromised resources or revoking access credentials, enhancing the speed and effectiveness of your incident response.
Review and Compliance
Ensure Compliance and Reporting
Leverage AWS Config: Use AWS Config for continuous monitoring and auditing of your AWS resources, ensuring compliance with internal security policies and external regulatory standards.
Automated Reporting: Set up automated reporting mechanisms using AWS services and custom Lambda functions to facilitate regular compliance audits and provide stakeholders with ongoing visibility into the security and compliance status.
Best Practices for Optimizing SIEM in AWS
The following best practices offers practical strategies to enhance the efficiency, security, and cost-effectiveness of your SIEM system.
Efficient Data Management
Data Minimization
Relevance of Data: Focus on collecting only the data that is directly relevant to your security needs. Use AWS IAM policies and resource tags to manage data access and streamline data collection, thus minimizing unnecessary data that could increase storage and processing costs.
Log Rotation and Retention Policies: Implement log rotation to manage the size and number of log files actively. Define clear retention policies that align with compliance requirements and business needs, using AWS lifecycle policies to automate the archival or deletion of outdated logs.
Streamlined Data Processing
Use of Filters and Transformers: Implement filters and transformers within AWS Lambda or during the data ingestion phase with services like AWS Kinesis Data Firehose, which can modify or filter incoming data streams to enhance data quality and reduce noise.
Efficient Correlation Rules: Design and implement correlation rules that effectively reduce false positives. Use AWS CloudWatch or Lambda to refine these rules continuously, ensuring that alerts are both accurate and actionable.
Enhancing Detection Capabilities
Continuous Rule Improvement
Regular Updates: Regularly update and refine detection rules to respond to new threats and changes in the environment. Utilize AWS Security Hub insights to stay informed about the latest threat landscapes and adjust your rules accordingly.
Customization: Customize detection rules to address the specific security contexts of your AWS environment, taking into account unique operational patterns and risk profiles.
Leveraging Machine Learning
Anomaly Detection: Deploy machine learning models within tools like Amazon GuardDuty to identify unusual behaviors and potential threats more effectively. Take advantage of GuardDuty’s built-in ML capabilities for advanced threat detection.
Behavioral Analytics: Implement behavioral analytics using Amazon SageMaker to create custom ML models that learn from your environment's data, detecting deviations from established patterns that might indicate security incidents.
Alert Management
Prioritization of Alerts
Severity Levels: Define and implement a structured severity level system for alerts using AWS Security Hub, which helps in prioritizing response efforts based on the criticality of the alert.
Alert Consolidation: Utilize AWS Lambda and Amazon SNS to consolidate alerts and reduce duplication, focusing response efforts on the most significant and potentially damaging issues first.
Effective Notification Systems
Escalation Paths: Develop clear escalation paths that define who gets notified and when. Configure Amazon SNS or other AWS services to automate notifications to the right stakeholders quickly.
Integration with Incident Management Tools: Ensure seamless integration of your SIEM system with incident management platforms such as AWS Systems Manager Incident Manager, facilitating efficient tracking and management of incidents.
Cost Optimization
Cost-Efficient Storage Solutions
Intelligent Tiering: Implement S3 Intelligent-Tiering to automatically move logs between different storage classes based on access patterns, optimizing costs without sacrificing data availability.
Data Compression: Apply data compression techniques before storing data. Use services like AWS Kinesis Data Firehose, which can compress data streams before storage, reducing storage volume and costs.
Monitor and Optimize Costs
Regular Reviews: Conduct regular reviews of your SIEM solution costs using AWS Cost Explorer. Identify and eliminate inefficiencies, and adjust your usage based on these insights.
Scaling Strategies: Implement scaling strategies for compute resources, like AWS Lambda, using AWS Auto Scaling to manage demand spikes effectively without permanent increases in cost.
Security and Compliance
Secure SIEM Assets
Access Controls: Apply stringent access controls using AWS IAM to manage who can access SIEM tools and data. Ensure that policies are least privileged, granting access only as necessary.
Encryption: Encrypt all sensitive data, both in transit and at rest, using AWS KMS to manage keys and encryption standards, ensuring data security across your SIEM infrastructure.
Compliance Audits
Continuous Compliance: Utilize AWS Security Hub to continuously monitor and ensure compliance with industry standards and regulations, integrating compliance checks into your daily operations.
Audit Trails: Maintain comprehensive audit trails for forensic investigations and compliance audits. Use AWS CloudTrail and other logging services to track all changes and access to SIEM resources.
Summary
The setup and optimization of a SIEM system in AWS can significantly enhance your organization’s ability to detect, analyze, and respond to security threats.
I encourage you to dive deeper into each section of this newsletter to understand the nuances of SIEM technologies and their implementation in AWS.
By doing so, you'll gain a more profound understanding of how to tailor SIEM solutions to fit your unique security needs and operational contexts.
Whether you're new to cloud security or looking to refine your existing SIEM setup, the insights provided here will help you build a more secure, responsive, and efficient security management system.
If you have any observations or views about this post, please leave a comment.
That’s it for today!
Did you enjoy this newsletter issue?
Share with your friends, colleagues, and your favorite social media platform.
Until next week — Amrut
Whenever you’re ready, there are 2 ways I can help you:
Are you thinking about getting certified as a Google Cloud Digital Leader? Here’s a link to my Udemy course, which has helped 597+ students prepare and pass the exam. Currently, rated 4.65/5. (link)
Course Recommendation: AWS Courses by Adrian Cantrill (Certified + Job Ready):
ALL THE THINGS Bundle (I got this. Highly recommend it!)
Note: These are affiliate links.
Get in touch
You can find me on LinkedIn or X.
If you wish to request a topic you would like to read, you can contact me directly via LinkedIn or X.


